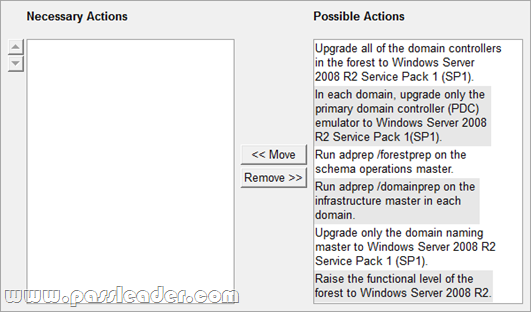
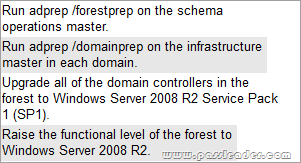
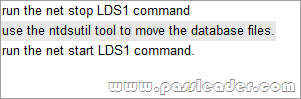
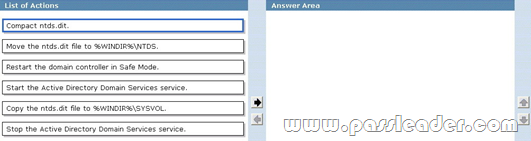
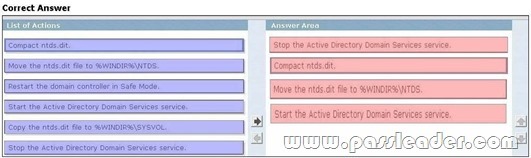
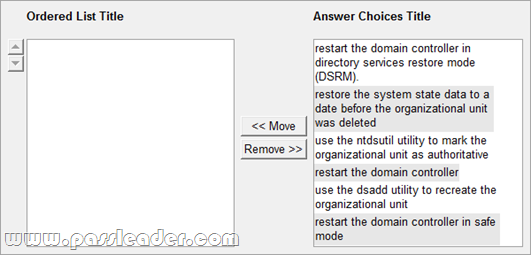
Where To Get The 100% Valid 70-640 exam dumps? Come to PassLeader! Here you can get the latest version 70-640 PDF dumps or VCE dumps, we guarantee our 651q 70-640 exam questions are the latest and you will get all the new questions and answers, which are not available on other wesites now! Now try our best 70-640 exam dumps with VCE and you will acquire your 70-640 certification exam immediately.
keywords: 70-640 exam,651q 70-640 exam dumps,651q 70-640 exam questions,70-640 pdf dumps,70-640 practice test,70-640 vce dumps,70-640 study guide,70-640 braindumps,TS: Windows Server 2008 Active Directory, Configuring Exam
QUESTION 261
Your network contains an Active Directory forest. The forest contains an Active Directory site for a remote office. The remote site contains a read-only domain controller (RODC). You need to configure the RODC to store only the passwords of users in the remote site. What should you do?
A. Create a Password Settings object (PSO).
B. Modify the Partial-Attribute-Set attribute of the forest.
C. Add the user accounts of the remote site users to the Allowed RODC Password Replication Group.
D. Add the user accounts of users who are not in the remote site to the Denied RODC Password Replication Group.
QUESTION 262
Your company has four offices. The network contains a single Active Directory domain. Each office has a domain controller. Each office has an organizational unit (OU) that contains the user accounts for the users in that office. In each office, support technicians perform basic troubleshooting for the users in their respective office. You need to ensure that the support technicians can reset the passwords for the user accounts in their respective office only. The solution must prevent the technicians from creating user accounts. What should you do?
A. For each OU, run the Delegation of Control Wizard.
B. For the domain, run the Delegation of Control Wizard.
C. For each office, create an Active Directory group, and then modify the security settings for each group.
D. For each office, create an Active Directory group, and then modify the controlAccessRights attribute for each group.
Answer: A
QUESTION 263
Your network contains a single Active Directory domain. Client computers run either Windows XP Service Pack 3 (SP3) or Windows 7. All of the computer accounts for the client computers are located in an organizational unit (OU) named OU1. You link a new Group Policy object (GPO) named GPO10 to OU1. You need to ensure that GPO10 is applied only to client computers that run Windows 7. What should you do?
A. Create a new OU in OU1. Move the Windows XP computer accounts to the new OU.
B. Enable block inheritance on OU1.
C. Create a WMI filter and assign the filter to GPO10.
D. Modify the permissions of OU1.
Answer: C
QUESTION 264
Your network contains an Active Directory domain named contoso.com. You need to audit changes to a service account. The solution must ensure that the audit logs contain the before and after values of all the changes. Which security policy setting should you configure?
A. Audit Sensitive Privilege Use
B. Audit User Account Management
C. Audit Directory Service Changes
D. Audit Other Account Management Events
Answer: C
QUESTION 265
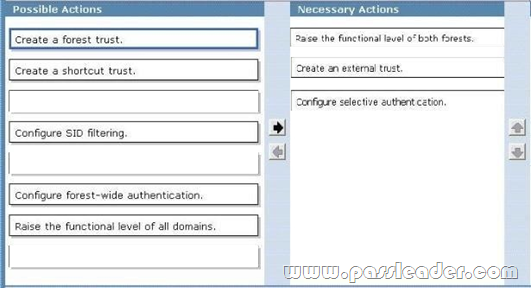
Your network contains two Active Directory forests named contoso.com and nwtraders.com. Active Directory Rights Management Services (AD RMS) is deployed in each forest. You need to ensure that users from the nwtraders.com forest can access AD RMS protected content in the contoso.com forest. What should you do?
A. Add a trusted user domain to the AD RMS cluster in the nwtraders.com domain.
B. Create an external trust from nwtraders.com to contoso.com.
C. Add a trusted user domain to the AD RMS cluster in the contoso.com domain.
D. Create an external trust from contoso.com to nwtraders.com.
Answer: C
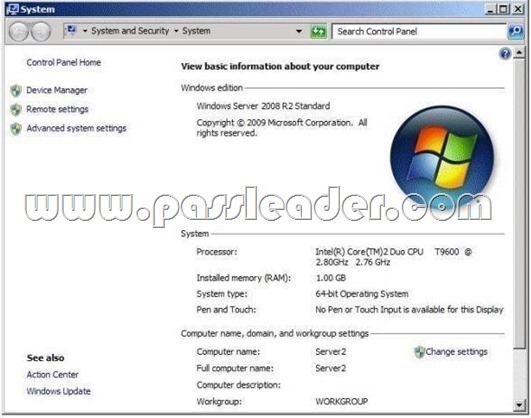
QUESTION 266
Your network contains a server named Server1 that runs Windows Server 2008 R2. Server1 is configured as an Active Directory Federation Services (AD FS) 2.0 standalone server. You plan to add a new token-signing certificate to Server1. You import the certificate to the server as shown in the exhibit. (Click the Exhibit button.)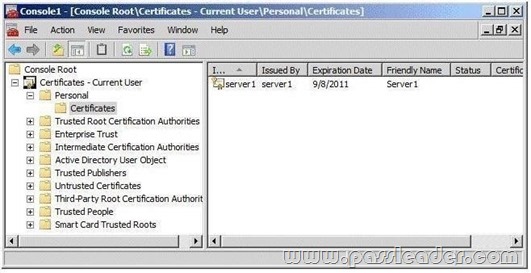
When you run the Add Token-Signing Certificate wizard, you discover that the new certificate is unavailable. You need to ensure that you can use the new certificate for AD FS. What should you do?
A. From the properties of the certificate, modify the Certificate Policy OIDs setting.
B. Import the certificate to the AD FS 2.0 Windows Service personal certificate store.
C. From the properties of the certificate, modify the Certificate purposes setting.
D. Import the certificate to the local computer personal certificate store.
Answer: D
QUESTION 267
You need to purge the list of user accounts that were authenticated on a read-only domain controller (RODC). What should you do?
A. Run the repadmin.exe command and specify the /prp parameter.
B. From Active Directory Sites and Services, modify the properties of the RODC computer object.
C. From Active Directory Users and Computers, modify the properties of the RODC computer object.
D. Run the dsrm.exe command and specify the -u parameter.
Answer: A
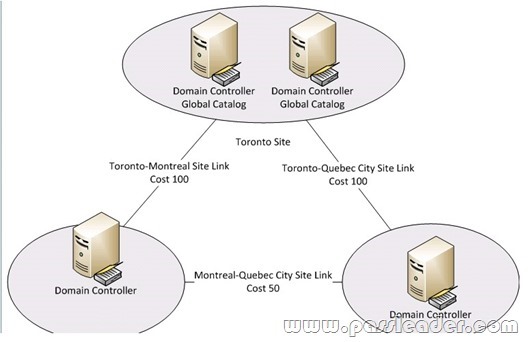
QUESTION 268
Your company has a main office and four branch offices. An Active Directory site exists for each office. Each site contains one domain controller. Each branch office site has a site link to the main office site. You discover that the domain controllers in the branch offices sometimes replicate directly to each other. You need to ensure that the domain controllers in the branch offices only replicate to the domain controller in the main office. What should you do?
A. Modify the firewall settings for the main office site.
B. Disable the Knowledge Consistency Checker (KCC) for each branch office site.
C. Disable site link bridging.
D. Modify the security settings for the main office site.
Answer: C
QUESTION 269
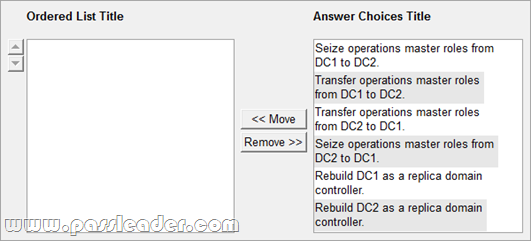
Your network contains an Active Directory forest. The forest contains one domain. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2008 R2. DC1 was installed before DC2. DC1 fails. You need to ensure that you can add 1,000 new user accounts to the domain. What should you do?
A. Modify the permissions of the DC2 computer account.
B. Seize the schema master FSMO role.
C. Configure DC2 as a global catalog server.
D. Seize the RID master FSMO role.
Answer: D
QUESTION 270
Your network contains an Active Directory domain named contoso.com. You need to identify whether the Active Directory Recycle Bin is enabled. What should you do?
A. From Ldp, search for the Reanimate-Tombstones object.
B. From Ldp, search for the LostAndFound container.
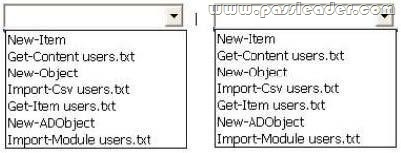
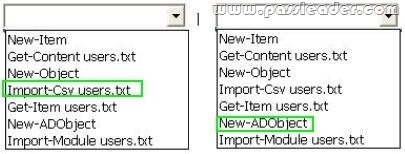
C. From Windows PowerShell, run the Get-ADObject cmdlet.
D. From Windows PowerShell, run the Get-ADOptionalFeature cmdlet.
Answer: D
http://www.passleader.com/70-640.html
QUESTION 271
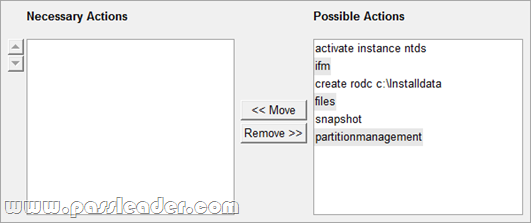
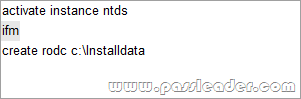
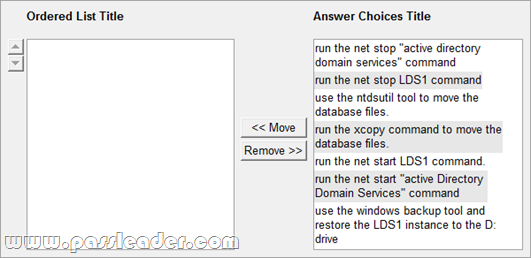
Your network contains an Active Directory domain. You create and mount an Active Directory snapshot. You run dsamain.exe as shown in the exhibit. (Click the Exhibit button.)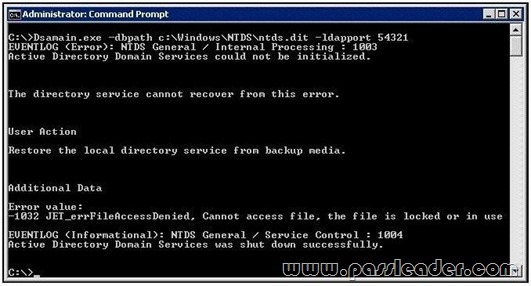
You need to ensure that you can browse the contents of the Active Directory snapshot. What should you?
A. Stop Active Directory Domain Services (AD DS), and then rerun dsamain.exe.
B. Change the value of the dbpath parameter, and then rerun dsamain.exe.
C. Change the value of the ldapport parameter, and then rerun dsamain.exe.
D. Restart the Volume Shadow Copy Service (VSS), and then rerun dsamain.exe.
Answer: B
QUESTION 272
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 and a domain controller named DC1. On Server1, you configure a collector-initiated subscription for the Application log of DC1. The subscription is configured to collect all events. After several days, you discover that Server1 failed to collect any events from DC1, although there are more than 100 new events in the Application log of DC1. You need to ensure that Server1 collects events from DC1. What should you do?
A. On Server1, run wecutil quick-config.
B. On Server1, run winrm quickconfig.
C. On DC1, run wecutil quick-config.
D. On DC1, run winrm quickconfig.
Answer: D
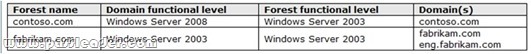
QUESTION 273
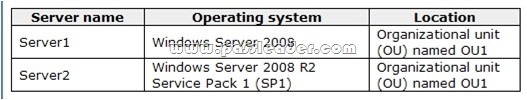
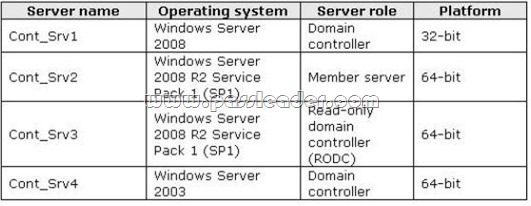
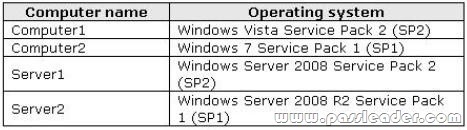
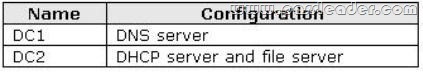
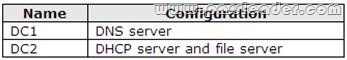
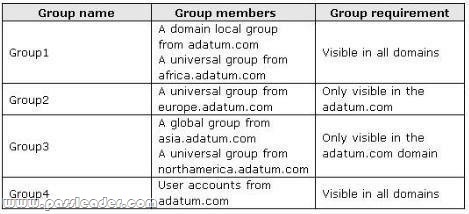
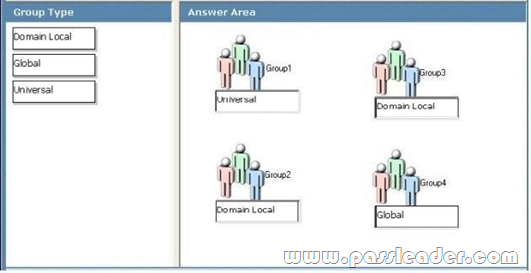
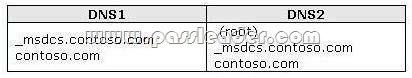
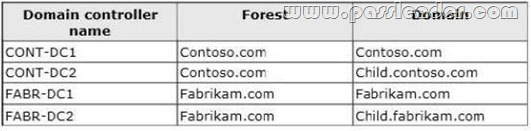
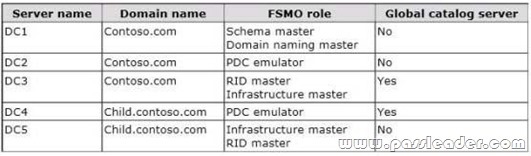
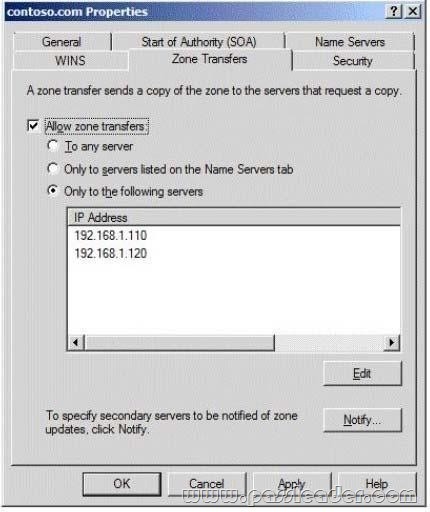
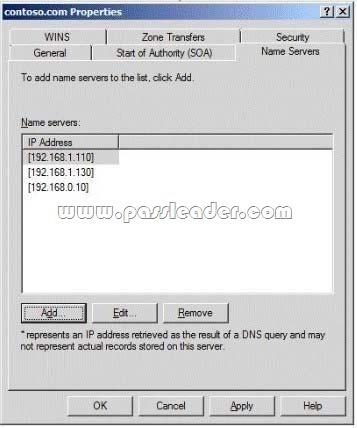
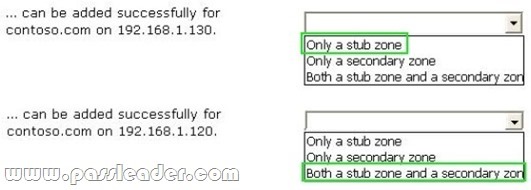
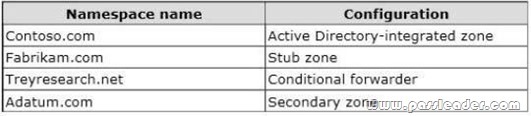
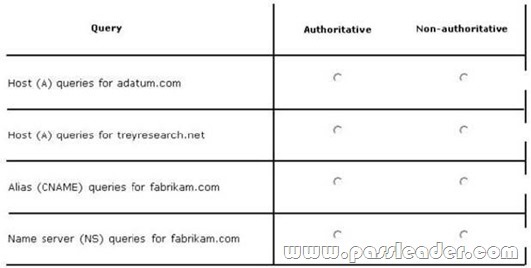
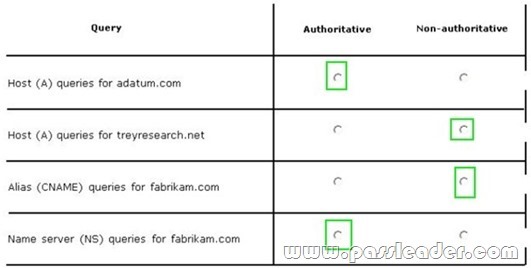
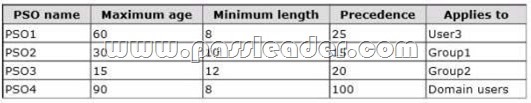
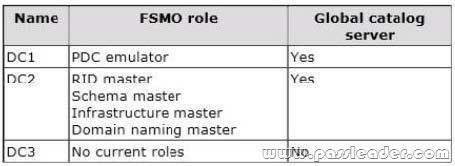
A network contains an Active Directory Domain Services (AD DS) domain. Active Directory is configured as shown in the following table.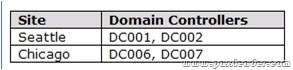
The functional level of the domain is Windows Server 2008 R2. The functional level of the forest is Windows Server 2003. Active Directory replication between the Seattle site and the Chicago site occurs from 8:00 P.M. to 1:00 A.M. every day. At 7:00 A.M. an administrator deletes a user account while he is logged on to DC001. You need to restore the deleted user account. You must achieve this goal by using the minimum administrative effort. What should you do?
A. On DC006, stop AD DS, perform an authoritative restore, and then start AD DS.
B. On DC001, run the Restore-ADObject cmdlet.
C. On DC006, run the Restore-ADObject cmdlet.
D. On DC001, stop AD DS, restore the system state, and then start AD DS.
Answer: A
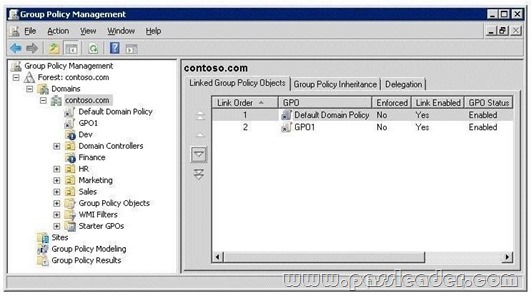
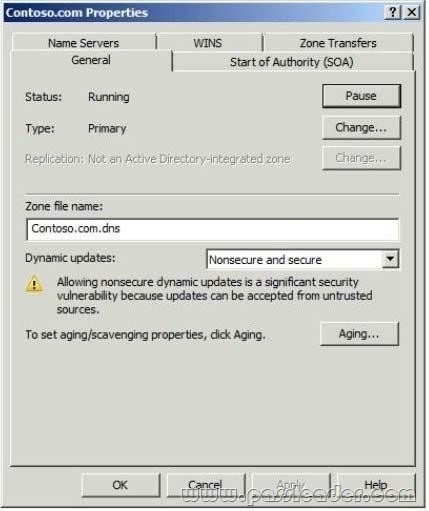
QUESTION 274
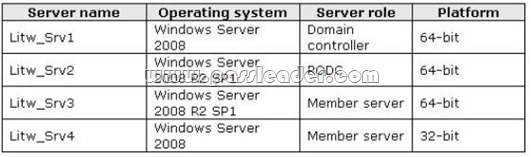
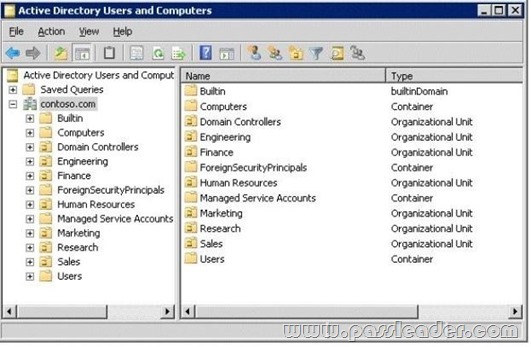
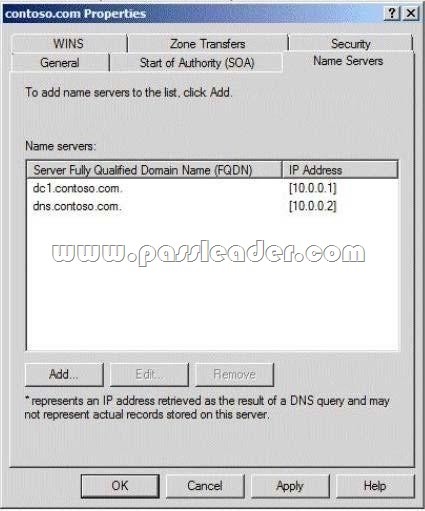
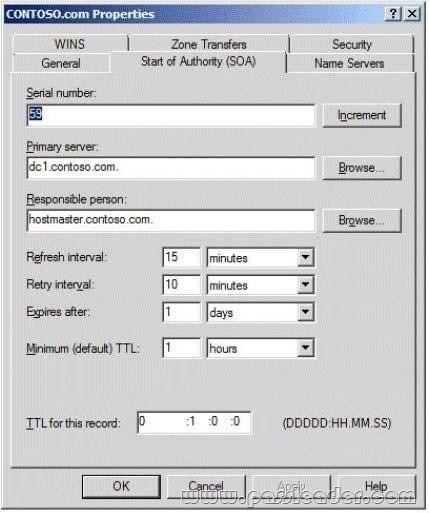
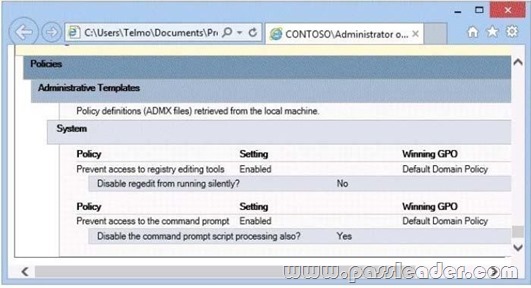
Your network contains an Active Directory domain. The domain is configured as shown in the exhibit.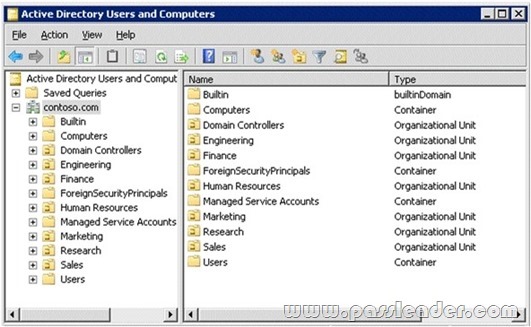
You have a Group Policy Object (GPO) linked to the domain. You need to ensure that the settings in the GPO are not processed by user accounts or computer accounts in the Finance organizational unit (OU). You must achieve this goal by using the minimum amount of administrative effort. What should you do?
A. Modify the Group Policy permissions.
B. Configure WMI filtering.
C. Enable block inheritance.
D. Enable loopback processing in replace mode.
E. Configure the link order.
F. Configure Group Policy Preferences.
G. Link the GPO to the Human Resources OU.
H. Configure Restricted Groups.
I. Enable loopback processing in merge mode.
J. Link the GPO to the Finance OU.
Answer: C
QUESTION 275
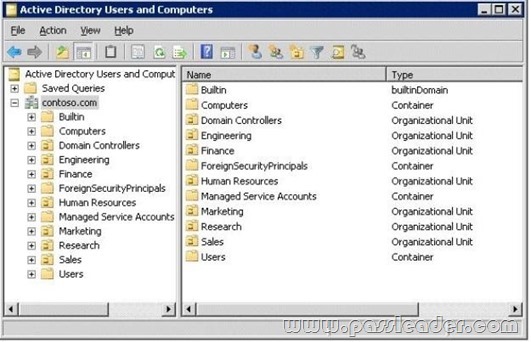
Your network contains an Active Directory domain named contoso.com. You have an organizational unit (OU) named Sales and an OU named Engineering. You have two Group Policy Objects (GPOs) named GPO1 and GPO2. GPO1 and GPO2 are linked to the Sales OU and contain multiple settings. You discover that GPO2 has a setting that conflicts with a setting in GPO1. When the policies are applied, the setting in GPO2 takes effect. You need to ensure that the settings in GPO1 supersede the settings in GPO2. The solution must ensure that all non-conflicting settings in both GPOs are applied. What should you do?
A. Configure Restricted Groups.
B. Configure the link order.
C. Link the GPO to the Sales OU.
D. Link the GPO to the Engineer OU.
E. Enable loopback processing in merge mode.
F. Modify the Group Policy permissions.
G. Configure WMI filtering.
H. Configure Group Policy Permissions.
I. Enable loopback processing in replace mode.
J. Enable block inheritance.
Answer: B
QUESTION 276
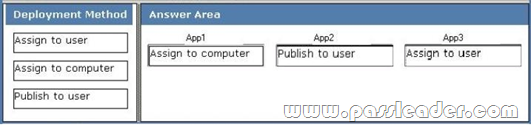
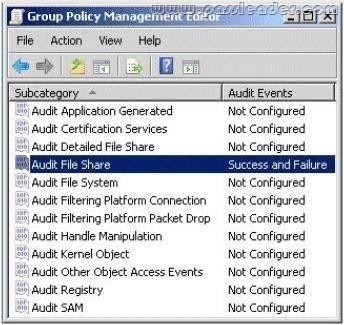
All vendors belong to a global group named vendors. You place three file servers in a new organizational unit (OU) named ConfidentialFileServers. The three file servers contain confidential data located in shared folders. You need to record any failed attempts made by the vendors to access the confidential data. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Create a new Group Policy Object (GPO) and link it to the CONFIDENTIALFILESERVERS OU.
Configure the Audit object access failure audit policy setting.
B. Create a new Group Policy Object (GPO) and link it to the CONFIDENTIALFILESERVERS OU.
Configure the Audit privilege use Failure audit policy setting.
C. On each shared folder on the three file servers, add the Vendors global group to the Auditing tab.
Configure Failed Full control setting in the AuditingEntry dialog box.
D. On each shared folder on the three file servers, add the three servers to the Auditing tab.
Configure Failed Full control setting in the AuditingEntry dialog box.
E. Create a new Group Policy Object (GPO) and link it to the CONFIDENTIALFILESERVERS OU.
Configure the Deny access to this computer from the network user rights setting for the Vendors global group.
Answer: AC
QUESTION 277
A corporate network includes a single Active Directory Domain Services (AD DS) domain. The HR department has a dedicated organizational unit (OU) named HR. The HR OU has two sub-OUs: HR Users and HR Computers. User accounts for the HR department reside in the HR Users OU. Computer accounts for the HR department reside in the HR Computers OU. All HR department employees belong to a security group named HR Employees. All HR department computers belong to a security group named HR PCs. Company policy requires that passwords are a minimum of 6 characters. You need to ensure that, the next time HR department employees change their passwords, the passwords are required to have at least 8 characters. The password length requirement should not change for employees of any other department. What should you do?
A. Modify the password policy in the GPO that is applied to the domain.
B. Create a new GPO, with the necessary password policy, and link it to the HR Users OU.
C. Create a fine-grained password policy and apply it to the HR Users OU.
D. Modify the password policy in the GPO that is applied to the domain controllers OU.
Answer: C
QUESTION 278
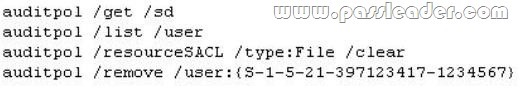
A corporate network includes a single Active Directory Domain Services (AD DS) domain. All regular user accounts reside in an organisational unit (OU) named Employees. All administrator accounts reside in an OU named Admins. You need to ensure that any time an administrator modifies an employee’s name in AD DS, the change is audited. What should you do first?
A. Create a Group Policy Object with the Audit directory service access setting enabled and link it to the Employees OU.
B. Modify the searchFlags property for the Name attribute in the Schema.
C. Create a Group Policy Object with the Audit directory service access setting enabled and link it to the Admins OU.
D. Use the Auditpol.exe command-line tool to enable the directoryservicechanges auditing subcategory.
Answer: D
QUESTION 279
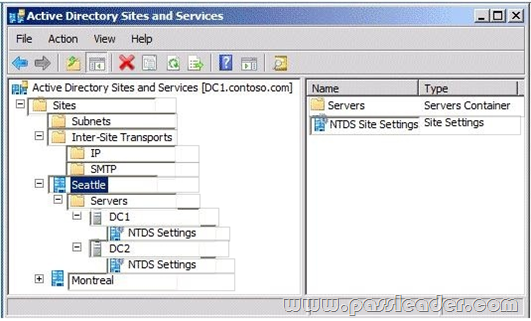
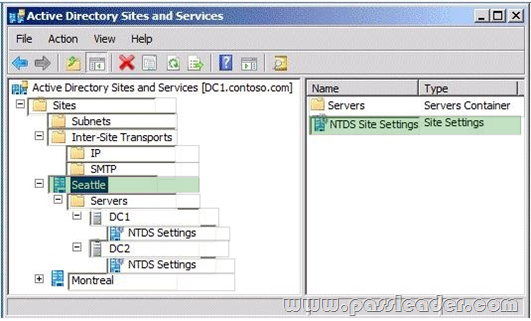
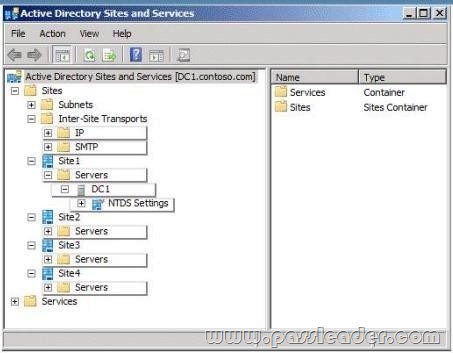
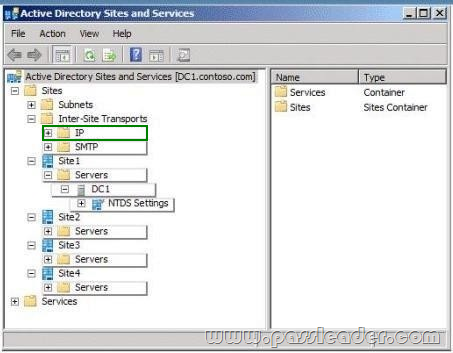
Your network contains an Active Directory forest named contoso.com. You need to provide a user named User1 with the ability to create and manage subnet objects. The solution must minimize the number of permissions assigned to User1. What should you do?
A. From Active Directory Users and Computers, run the Delegation of Control wizard.
B. From Active Directory Administrative Centre, add User1 to the Schema Admins group.
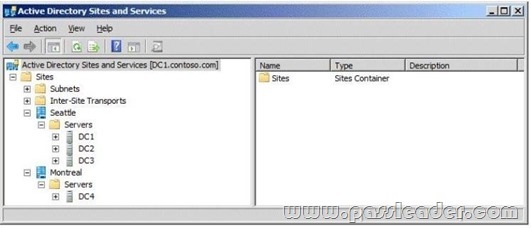
C. From Active Directory Sites and Services, run the Delegation of Control wizard.
D. From Active Directory Administrative Centre, add User1 to the Network Configuration Operators group.
Answer: C
QUESTION 280
A corporate network contains a Windows Server 2008 R2 Active Directory forest. You need to add a User Principle Name (UPN) suffix to the forest. What tool should you use?
A. Dsmgmt.
B. Active Directory Domains and Trusts console.
C. Active Directory Users and Computers console.
D. Active Directory Sites and Services console.
Answer: B